Cyber resilience: the gateway to new-age data security

Experts argue and rightly so that cyber resilience is more than a mere buzzword today. It has been and will always be relevant. As any business grows and modernizes, it demands higher and more efficient governance. A cyber resilience framework pertains to end-to-end governance to keep the security of the business intact. In fact, cybersecurity and resilience solutions are among the most sought-after managed cyber services of all times. Compromised data security has always been heavily taxing.
According to recent research, cybercrime damage is expected to reach $8 trillion USD by 2023. Is your organization part of this pool or does it stand aside?
Technology comes with its own pluses and minuses. It brings with it tons of opportunities to grow but also carries some challenges that cannot be overlooked. As enterprises embrace modern ways of conducting business and move closer to digitization, vulnerabilities associated with data and technology increase. The rising number of data breaches and cybersecurity incidents is a warning for businesses around the world to rethink their risk management strategies.
Today, companies need more than just an information security plan or governance policy to fight hacks and cyber-attacks. They need end-to-end managed cyber services to prevent security incidents, including a bulletproof action plan to counter them when needed. And, that’s where cyber resilience solutions come into the picture.
What is cyber resilience?
Simply put, cyber resilience is the ability of organizations to withstand cybercrime, prepare for possible threats, and build an action plan to recover from it if it ever hits them. It is a comprehensive framework that aims to protect the entire organization, including its people, processes, and information from cyber crises. The holistic integration of managed cyber services can help you plan this strategically.
Govern. Mitigate. Comply.
Build a structured GRC framework to ensure business continuity and regulatory adherence.
How is cyber resilience different from cybersecurity solutions?
Broadly speaking, cyber resilience and cyber security sound synonymous. The two terms are closely related, but cannot be used interchangeably. While cybersecurity mainly focuses on protecting business information, cyber resilience solutions are about protecting the business from attacks that can potentially disrupt the entire operation. Cyber resilience is a more integrated and proactive approach that includes cybersecurity as a key element.
How is cyber resilience different from cybersecurity solutions?
Broadly speaking, cyber resilience and cyber security sound synonymous. The two terms are closely related, but cannot be used interchangeably. While cybersecurity mainly focuses on protecting business information, cyber resilience solutions are about protecting the business from attacks that can potentially disrupt the entire operation. Cyber resilience is a more integrated and proactive approach that includes cybersecurity as a key element.
But, why should you care?
Almost all data-driven organizations have a governance policy or risk management framework in place. You would too. But given the big data breaches at companies like Facebook and Equifax, do you feel good about your security measures?
As your data and business scale, cyber threats increase accordingly. Your business is vulnerable to threats like sensitive data theft, insider breaches, poorly managed processes, and technology-driven attacks. In this high-risk digital landscape, attacks can happen anytime, anywhere. A cyber resilience framework can protect you from security incidents over the long term without disrupting business operations. A skilled cyber managed service provider can help.
Watch: Actionable Data Governance: How to manage my sensitive data risk?
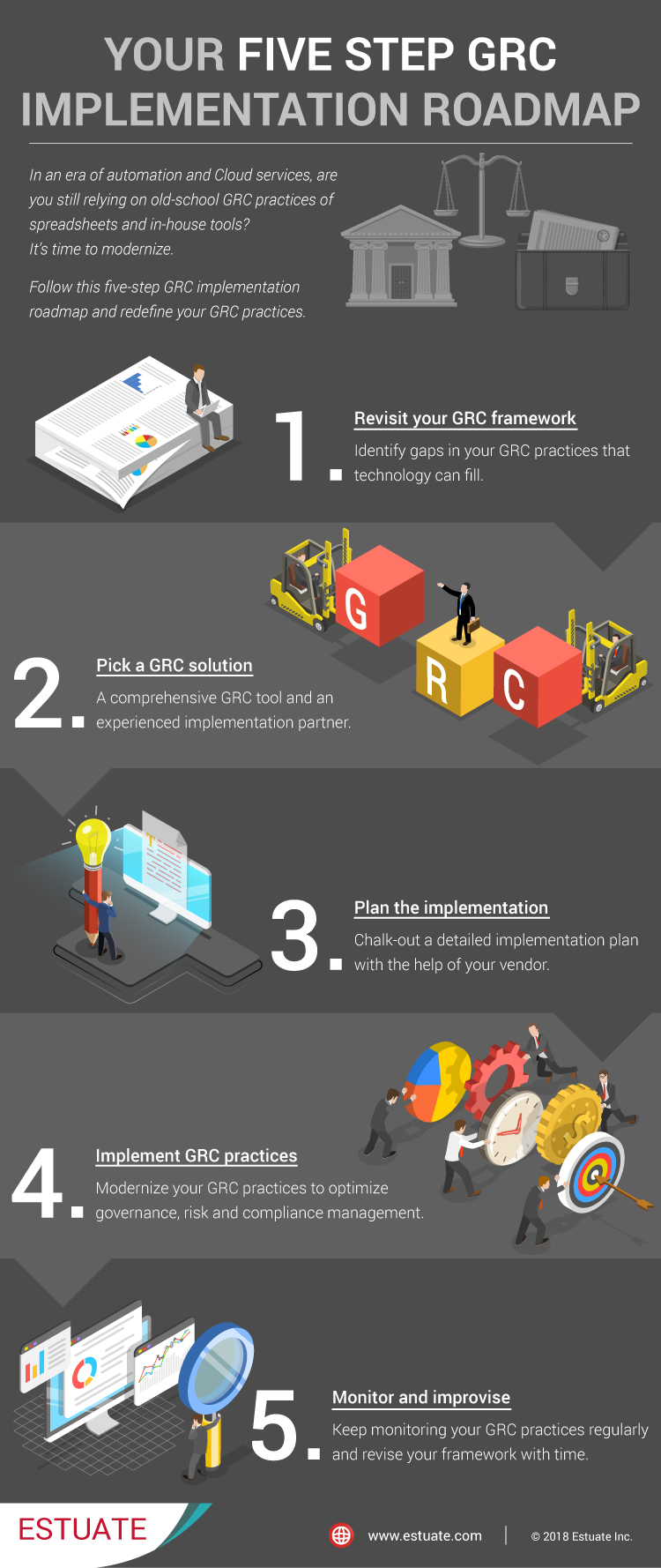
How to achieve cyber resilience in your organization?
- Identify the weak spots
- Protect the critical IT assets
- Detect the early signs of malpractice
- Respond with immediate effect
- Recover as holistically as possible
Step 1: Identify the weak spots
For a scalable cyber resilience strategy framework, you must first take a closer look at your organization’s vulnerabilities. Where is all your sensitive information stored? Who are the people working with sensitive business information? What equipment is used to perform sensitive processes? Conduct a thorough hygiene check of your business and identify the areas where cyber resilience solutions are urgently needed.The first step to avoiding a data breach in your enterprise is thorough internal awareness.
Step 2: Protect the critical IT assets
Once you have identified your most critical assets and processes, you need to develop a strategy to protect them from cybercrime. This includes changing security policies, strengthening device encryption, limiting unauthorized use of external devices, educating employees on the importance of cybersecurity solutions, and implementing best practices to prevent malicious activity.
The increasing influx of new technologies makes this step even more important. Take blockchain, for instance. The advent of blockchain has revolutionized the cybersecurity solutions space.
Step 3: Detect the early signs of malpractice
In addition to proactively preventing cybercrime, you must also closely monitor your business processes, employee activities, and sensitive information. Early detection of fraud or malware can minimize the drastic impact on business operations. Any troubling activity must be reported immediately and appropriate action must be taken.
Strict and timely adherence to these steps can help your business with cyber resilience
Step 4: Respond with immediate effect
Cybercriminals are never at rest, and despite the security measures taken, your company can experience a security incident. It could be something as minor as an employee using a personal device for an official task, or as major as the loss of sensitive customer data. As soon as suspicious activity of any kind is uncovered, it must be dealt with immediately and forwarded to the right people in the company to combat it effectively.
Step 5: Recover as holistically as possible
What’s done is done, but you can always mitigate the adversity of cybercrime with the right measures. This step is about the measures that can be taken to ward off malicious activities, prevent them from spreading to different departments, and fix the bug under your control.
The aftermath of a security incident can be devastating. Not only does it hinder business activities, but the company suffers huge financial losses and its brand value is severely impacted. A bulletproof cybercrime prevention strategy is a must for all businesses, regardless of size or type. Cyber resilience is a smart choice to protect your business data, processes, technologies, and employees from cybercrime in the long run.
As most data-driven enterprises today center on software applications, a data protection strategy can prove to be handy. When holistic and properly deployed, such a strategy can form the bedrock for your application testing.
Watch the webinar: Securing and protecting enterprise data.
Unlock robust cyber resilience solutions with Estuate’s GRC framework
We integrate all three pillars of GRC under one umbrella to help you enhance business efficiencies.
- Corporate Governance
- Policy creation and management
- Development of a legal and regulatory framework
- Information and asset management
- Enterprise-wide information security awareness
- Risk Management
- Business and IT risk assessment
- Risk monitoring and analysis
- Third-party risk management
- Issue management and troubleshooting
- Regulatory Compliance
- Regulatory intelligence
- Compliance design
- Compliance audits and surveys
- Reporting and metrics
Simplify. Secure. Sustain.
Elevate your governance, risk, and compliance strategy with expert solutions.
Let’s Talk!
Want to explore further? Dive in here to learn more about our overall GRC ambit
Our GRC solution span covers a wide gamut of specializations: from Cisco, Imperva, Auryc, and more.
So if you are looking for any assistance in the realm of managed cyber services, we’ll be more than happy to help!