The Art of Masking Data: Safeguarding Privacy in a Networked World

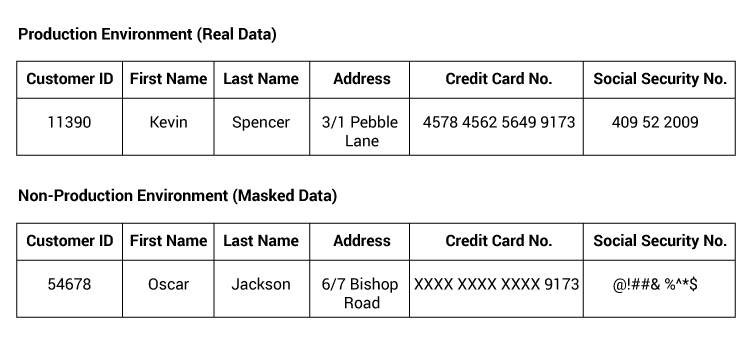
In today’s digital age, organizations rely on interconnected applications to streamline operations and enhance productivity. However, this interconnectedness poses a significant challenge when it comes to data privacy. It is essential to mask data consistently across all applications to safeguard sensitive information while enabling comprehensive and meaningful data testing.
In this blog post, we will delve into the importance of data masking, explore the challenges organizations face in maintaining data privacy, and showcase how IBM Optim can address these concerns. Through a real-world case study, we will demonstrate the power of IBM Optim in achieving consistent data masking across applications.
I. The Significance of Consistent Data Masking
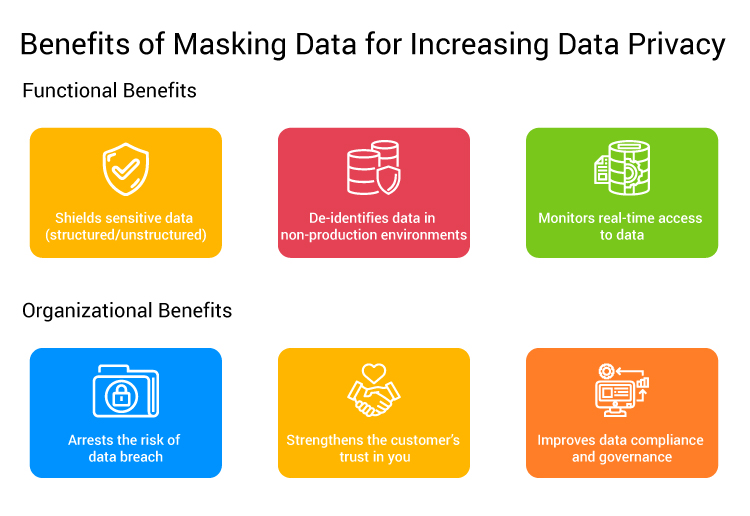
In a midsized or large organization, the proliferation of production databases and highly networked business solutions necessitates a robust data privacy strategy. Data masking plays a pivotal role in protecting sensitive information by replacing original data with fictional, yet realistic, data. Consistent data masking ensures that all applications sharing data can be tested together effectively, using meaningful datasets while preserving confidentiality. This approach is crucial in complying with data privacy regulations, safeguarding customer information, and mitigating the risk of costly data breaches.
II. Challenges of Data Masking in a Networked Environment
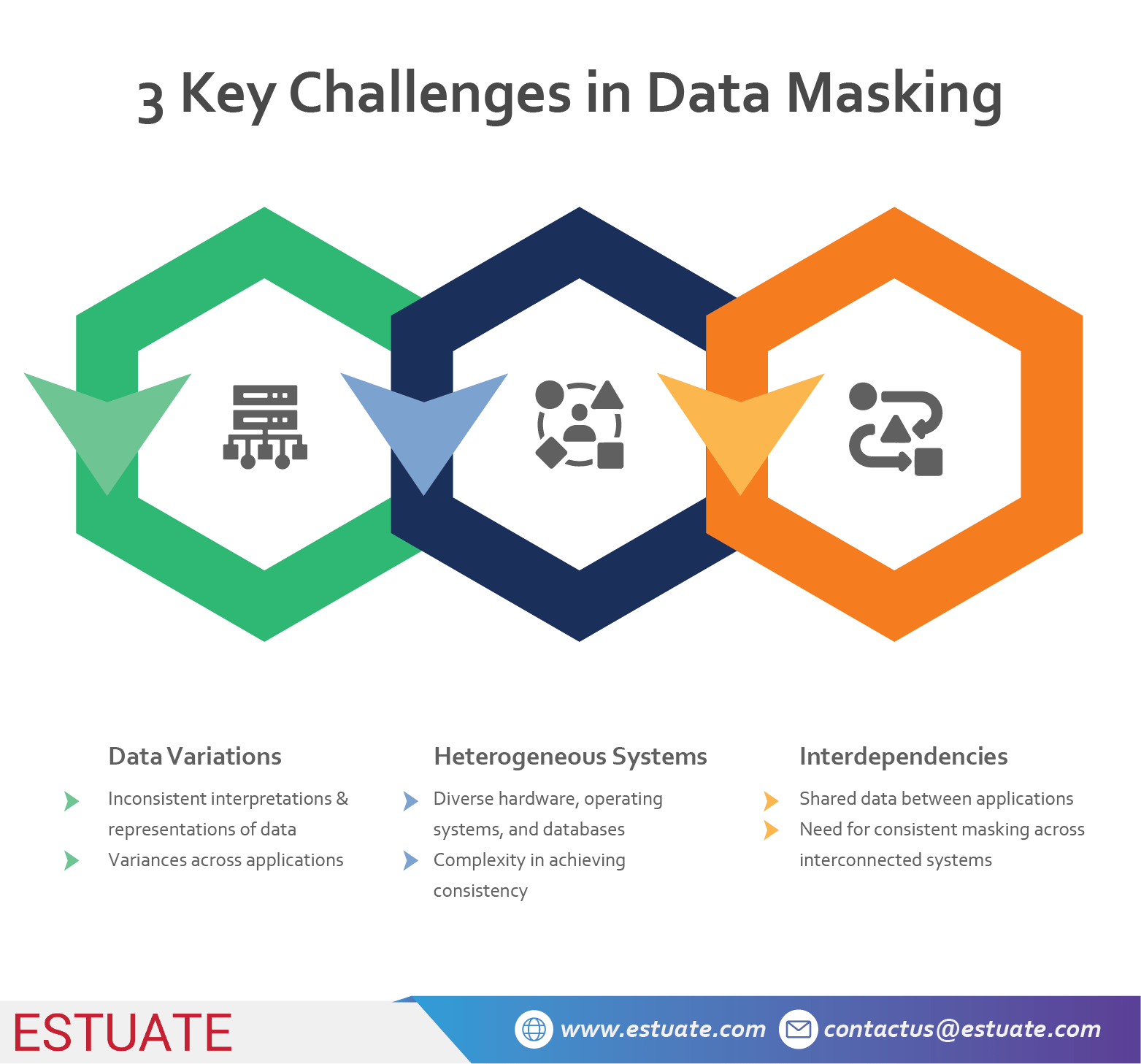
In a networked environment, where multiple applications share data, ensuring consistent data masking can be complex. Organizations face several challenges, including:
a. Data Variations
Different applications may interpret and store data differently. Variances in field lengths, data formats, or data representations can make it challenging to achieve consistent data masking across applications.
Key Challenges in Data Masking
b. Heterogeneous Systems
Applications may run on diverse hardware, operating systems, or databases. Ensuring consistent mapping algorithms across these heterogeneous systems is critical to maintaining data privacy during testing.
c. Interdependencies
Many applications rely on shared data, making it crucial to mask the data consistently across all interconnected systems. Failure to do so may result in incomplete or inaccurate test results.
Data masking is a pivotal strategy for protecting sensitive information and ensuring meaningful data testing in today’s interconnected business landscape.
III. Case Study: Data Masking Across PeopleSoft and Oracle
E-Business Suite
To illustrate the importance of consistent data masking, let’s examine a real-world scenario. A major pharmaceutical company approached Estuate with a significant data privacy challenge. The company needed to share employee data across its PeopleSoft and Oracle E-Business Suite applications while ensuring consistent data masking for comprehensive testing.
The company was already leveraging IBM Optim to protect data in its PeopleSoft application and wanted to extend its usage to Oracle. The primary objective was to mask data consistently in both applications, allowing for seamless end-to-end testing processes without compromising sensitive information. The project involved the following steps:
a. Identifying Common Data Elements
The Estuate team analyzed the data structures of PeopleSoft and Oracle to identify common data elements. This step was crucial in understanding the shared data that required consistent masking across both applications.
b. Addressing Data Definition Variations
Each enterprise system may have its unique way of representing data. Estuate carefully examined the variations in data definitions between PeopleSoft and Oracle and developed a strategy to ensure consistent masking, considering differences in field lengths, formats, and data representations.
c. Leveraging IBM Optim
Estuate utilized the powerful capabilities of IBM Optim to execute the data masking project. A job was built in IBM Optim to extract data from the company’s HR database. The team then masked eight columns of the data, verified the masked data against the corresponding PeopleSoft database, and provided knowledge transfer to the company’s staff.
IV. The Benefits of IBM Optim Data Masking
Implementing IBM Optim’s data masking solution offered significant advantages to the pharmaceutical company:
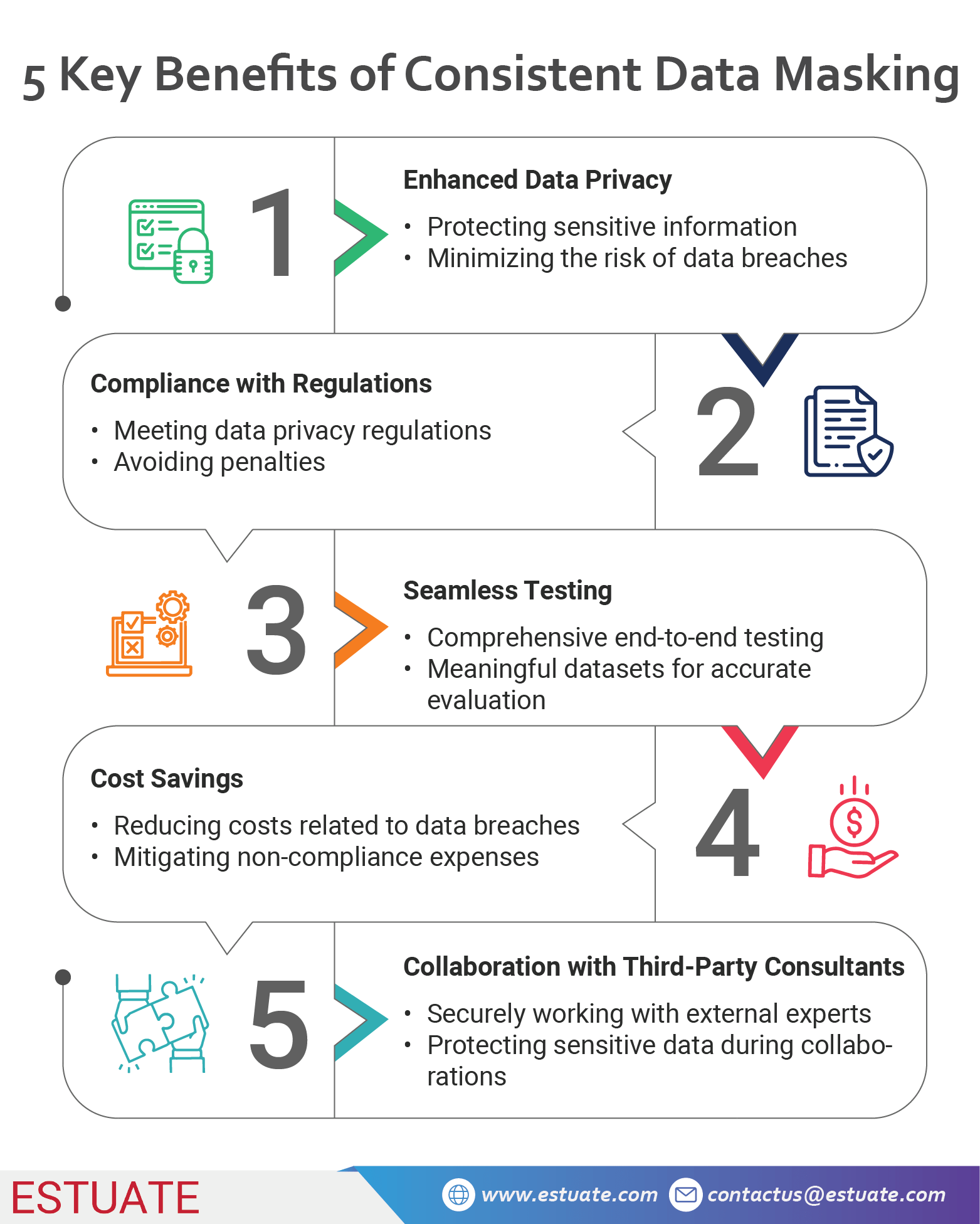
a. Enhanced Data Privacy
By consistently masking sensitive data across PeopleSoft and Oracle E-Business Suite, the pharmaceutical company ensured that confidential employee information remained protected. This proactive approach to data privacy minimized the risk of unauthorized access or data breaches.
Discover the advantages of implementing consistent data masking
b. Compliance with Data Privacy Regulations
With data privacy regulations becoming increasingly stringent, organizations must comply with various mandates such as GDPR or CCPA. IBM Optim’s data masking solution helped the pharmaceutical company meet these compliance requirements by anonymizing personal and sensitive data during testing, reducing the risk of non-compliance and potential penalties.
c. Seamless End-to-End Testing
By ensuring consistent data masking across applications, the pharmaceutical company was able to conduct comprehensive end-to-end testing. Testing scenarios involving both PeopleSoft and Oracle E-Business Suite applications could be performed using meaningful datasets, enabling accurate evaluation of system interactions and ensuring a higher quality of software releases.
d. Cost Savings
By utilizing IBM Optim’s data masking capabilities, the pharmaceutical company significantly reduced the potential costs associated with data breaches or non-compliance penalties. The investment in data privacy solutions proved to be a cost-effective approach compared to the potential financial and reputational damage resulting from data leaks.
e. Collaboration with Third-Party Consultants
The ability to mask data consistently across applications also facilitated collaboration with third-party consultants. The pharmaceutical company could confidently engage external experts, knowing that the sensitive data shared with them would be appropriately protected. This fostered a productive and secure working environment.
By leveraging IBM Optim, organizations can comply with data privacy regulations and confidently collaborate with third-party consultants while maintaining the security of sensitive data.
In today’s interconnected business landscape, consistent data masking across applications is crucial for maintaining data privacy and enabling meaningful testing. IBM Optim provides a powerful solution to address the challenges organizations face in protecting sensitive information while ensuring comprehensive testing. Through a real-world case study, we saw how a pharmaceutical company successfully implemented IBM Optim to mask employee data consistently across PeopleSoft and Oracle E-Business Suite. By leveraging IBM Optim’s capabilities, the company achieved enhanced data privacy, compliance with regulations, seamless testing processes, cost savings, and secure collaboration with third-party consultants. Embracing robust data masking solutions is vital for organizations aiming to navigate the complexities of data privacy in a highly networked environment.