
Modern businesses feed on data for breakfast, lunch, and dinner. Today, so significant is good clean data for business growth that even the minutest of data compromise is capable of wreaking havoc on brand positions. Daily headlines on data leaks and thefts bear testimony to this. Goes without saying, this has ushered privacy tactics like data masking straight into today’s council of big data management solutions. If you have only been opting for data archiving solutions to uphold data integrity till date, right now would be the right time to go ahead and opt for data privacy as a service as well.
Remember Quora’s 2018 mega data breach or the more recent MyRepublic data leak? The shock waves these events triggered were massive at both the business and customer levels.
Opting for data privacy as a service and masking data can save your business from such undesirable scenarios.
What is Data Masking?
Data masking is a smart way of creating ‘realistic fake’ data. This fictionalized data is similar to its real counterpart albeit encrypted, shuffled, substituted, or tweaked in some other way. The ingenuity of this big data management solution is that it ably caters to all your functional needs (training, testing, auditing, etc.) while simultaneously protecting the sensitive information from unintended users. As and when needed, the data can always be engineered back to its original state.
For instance, when testing a net banking application for quality, testers need to log in as a user and process transactions – putting confidential customer information at the risk of exposure/misuse. However if the data is masked in the non-production testing environment, the risk can be easily averted.
Textbook examples of business data that require masking are corporate intelligence assets and personally identifying information (PII) like full names, email addresses, and national identifiers of personnel, customers, or business partners.
Such careful data governance along with other data management hacks like data archiving can make a world of difference for your business.
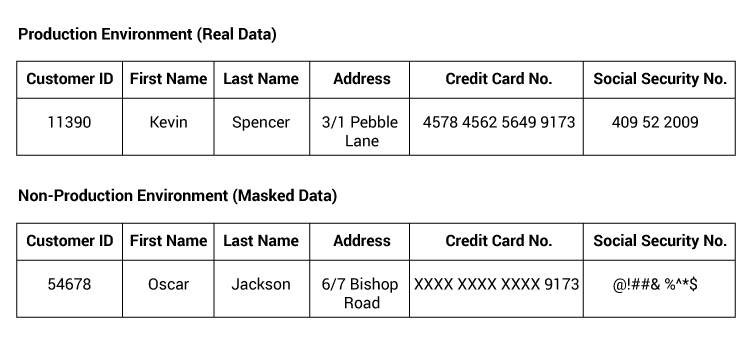
Non-Production Data Masking: Part of Big Data Management Solution
Understanding Data Masking Needs – Why Should You Put a Mask on Data?
Data is a multi-dimensional and multi-utility business resource. It is present everywhere from your CRM software to the third-party interfaces you are affiliated with, making it one of the most vulnerable company assets. Toward this, robust big data management solutions recognize masking and data archiving as quintessential for protecting overall data integrity.
You can unlock the following capabilities at the functional level with data masking solutions in place:
Shield sensitive data (structured/unstructured)
All thanks to the big data boom, research suggests that by 2025, the global data bank will exceed a staggering volume of 180 zettabytes! For businesses, this means a rapidly expanding inventory of information stored across structured databases and unstructured image files, documents, forms, etc. You must have the flexibility of protecting your sensitive data irrespective of its nature and also divulging it to desired shareholders as needed.
De-identify data in non-production environments
Non-production databases (development, testing, training) are highly vulnerable in nature. Methods that protect production environment live data (multi-factor authentication schemes, biometrics, etc.) cannot simply be applied here as the privacy pre-requisites of non-production data are often unique.
Data masking is necessary to be adopted under such scenarios.
Monitor real-time access to data
Certain databases are so confidential that they require 24*7 monitoring to control who is accessing them. Data privacy as a service can help here by masking data or terminating connections by analyzing access patterns.
At the organizational level, data privacy as a service is equally empowering. It helps you to:
Arrest the risk of data breach
This is perhaps the most crucial advantage of having a data masking solution in place. By shielding confidential information, you can keep the risks of data loss, insider threats, and privacy violations at bay. A sound data masking solution de-identifies the data in such a robust way that even if the data is lost or stolen, the perpetrator will not be able to derive any benefit from it.
Here are some other proven ways of avoiding data breach at your enterprise.
Strengthen the customer’s trust in you
Skyrocketing cases of data leak and identity theft have been emphasizing the need for data privacy as a service. Data breach does not only affect your brand equity and revenue, but it also upsets your entire business growth by disturbing the value you provide to your customers. A study of retail banking customers found that the latter prefer engaging only with brands that can safeguard their privacy.
Improve data compliance and governance
It is not enough to only secure data internally, businesses also need to protect sensitive data that may be exposed during third-party audits. With data masking solutions in place, it would always be easy to level up on these fronts. Pre-defined actionable data privacy classifications and rules help to increase compliance preparedness.
Benefits of Masking Data for Increasing Data Privacy
Welcome to the World of IBM – InfoSphere Optim Data Privacy as a Service
One thing that often bemuses most businesses is the universality of data. They are often not fully aware of all the pockets where confidential data resides or how exactly to protect the same. Identifying this need, IBM had added the InfoSphere Optim Data Privacy Solution in its ambit. It pertains to an end-to-end data privacy and governance solution across on-premise or cloud applications, reports, and databases – irrespective of the level of complexity of the associated IT environment. Like its test data management and data archiving solutions, data privacy as a service is another stellar offering from the IBM family.
Shared below is a quick summary of the capabilities it offers.
A Good Data Masking Solution? Here’s What to Expect –
- Composite data masking techniques – e.g., substrings, arithmetic expressions, random or sequential number generation, date aging, concatenation
- Coherence with the application for which it is masking data – it must adhere to permissible structures, values, and patterns; masked data must make functional sense to the recipients
- Pre-defined capabilities for masking standard customer data like national identifiers, email addresses, etc.
- Data coherence and integrity – the masking procedure must be scalable across all related databases and applications to avoid erroneous test results
- Flexibility – there should be provisions to mask the data before loading into non-production environments
Estuate has best-in-class expertise in IBM Data Privacy Implementation Solutions
In the wake of big data management, we understand the importance of maintaining data sanctity. With our expert IBM Optim data privacy capabilities, safeguard your sensitive data in non-production environments.
- We are IBM’s go-to partner for IBM Optim solutions across many platforms and use cases.
- We have a successful track record with over 350 Optim implementations.
- We have in-house domain experts to provide business-specific consultation across various industry verticals.
Watch this webinar conducted by Estuate’s IBM specialists on data privacy concerns in the gaming industry.
If you are looking for robust data privacy as a service, we would be more than happy to help. We’re just this click away.
What are your thoughts on data privacy as a service? Do you think that masking data can help your business?